Articles
Malware Analysis Exercise in CloudShark
6 min read
Hi all! Tom here. I’ve been working through more of the traffic analysis exercises posted at malware-traffic-analysis.net. These exercises have been a great way to learn how to jump to packet captures first when looking at a potential malware attack.
I found them really fun to go through and really digging deep into specific examples of malware and how it infects hosts and networks. We wanted to share some of our analysis from these exercises and how we can use CloudShark to solve it!
Here is our solution to the 2017-09-19 malware traffic analysis exercise.
The exercise Here is a link to the capture on CloudShark:
https://www.cloudshark.org/captures/079e4590c1eb
In this exercise we are given the PCAP, an e-mail, and the malware that infected a machine. The our tasks for this exercise are to find:
- Date and time of the activity (in GMT or UTC)
- The account name or username from the infected Windows computer
- The host name of the infected Windows computer
- The MAC address of the infected Windows computer
- SHA256 file hashes from the associated files
- A summary of what happened
Our solution
Date and time of the activity
Here we can use some metadata from the capture. After opening the capture on CloudShark we can click the more info link to find the start time, end time, and the duration of the capture. From here we see:
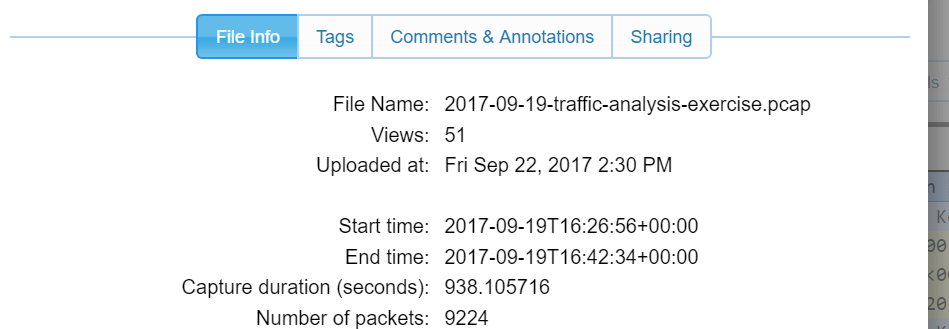
Granted this is the time information about the overall capture, but we can probably guess this is what we’re looking for since the capture isn’t that large.
Information about the infected machine
The username from the infected Windows computer is actually in a screen shot posted with the exercise. The username is Grace.Kelly.
The host name can be found by looking at the Ethernet endpoints found in the capture. Clicking each row to see the traffic sent by that address we can find only one host. The other Ethernet endpoint that belongs to a single host is the router.
Examining the traffic from this host we find the host name is KELLY-PC. The MAC address is 00:22:15:63:c9:5a for this host.
File hashes
To find this, we can submit the files to VirusTotal. In their report we find that the SHA256 hashes are:
- 6068741003028.XLS: 9b4e631b3a41b0a9feea26dedf363731eb851b77b20b6caebf9f5394281c111d
- ABF6AB.exe: b7dee12df4e82bbf11c73443f4371977caa38ada969256ac0f7973f2bf9e51ee
Looking at the e-mail we find that the 6068741003028.xls file was sent to grace.kelly.2001@yahoo.com. So, we look at the HTTP and SSL requests made in this capture to see if there is traffic that indicates this. We do see some SSL traffic to mail.yahoo.com and login.yahoo.com so this capture might include when the user got the malicious e-mail and executed the attachment that infected her computer.
Using reverse.it
The reverse.it site will run programs in a sandbox environment to analyze malicious files and report on them. Here is the report for the XLS file that was found in the e-mail sent to grace.kelly.20001@yahoo.com:
Here in the Extracted Files section we find an executable file that has a SHA256 sum that matches the malware found on the infected computer. In the HTTP section we also find a GET request to i.cubeupload.com. We can look for traffic in our PCAP by searching for HTTP packets to i.cubeupload.com.
How do we find what happened?
The follow stream analysis tools shows us that the HTTP GET was responded to by redirecting to https://u.cubeupload.com/1MDiPJ.jpg and we also find an HTTPS connection to this host and what looks to be a file download. Here we can verify that this XLS file is what infected the host.
Opening the Threat Analysis all of the threats mention a Loki Bot and we see threats indicating that application credentials were sent. We also see mention of the Loki Bot sent requests for C2 Commands indicating the bot was asking for commands from a CnC server.
The results
The machine named Kelly-PC was infected by a malicious e-mail that the user Grace.Kelly received that resulted in the host becoming part of a Loki Botnet.
Doing some research on Google for more information about this Loki-Bot we can find an in-depth analysis on this particular type of bot written by Rob Pantazopoulos and published by SANS. It turns out Rob actually wrote the rules that triggered the results found in the threat analysis tool! This write-up is incredibly in depth and discusses not only the network traffic sent by a host infected with this malware but also the techniques used to install it and avoid detection. Rob even wrote a python program called loki-parse “just for fun”.
Well as a last step “just for fun” we ran this program on our PCAP and found all the information sent from our infected host back to the CnC server. Here is what we found:
**************************************************************************
*************Decompressed Application/Credential Data [Start]*************
**************************************************************************
ldhttps://login.yahoo.com/account/challenge/password(robert1234@yahoo.comdhcvcgdajjdkdhttps://login.yahoo.com/account/challenge/password(robert1234@yahoo.comdhcvcgdajjdk
**************************************************************************
**************Decompressed Application/Credential Data [End]**************
**************************************************************************
{
"Compromised Host/User Data": {
"Compressed Application/Credential Data Size (Bytes)": 126,
"Compression Type": 0,
"Data Compressed": true,
"Encoded": false,
"Encoding": 0,
"Original Application/Credential Data Size (Bytes)": 376
},
"Compromised Host/User Description": {
"64bit OS": true,
"Built-In Admin": false,
"Domain Hostname": "Kelly-PC",
"Hostname": "KELLY-PC",
"Local Admin": true,
"Operating System": "Windows 7 Workstation",
"Screen Resolution": "1920x1080",
"User Name": "Grace.Kelly"
},
"Malware Artifacts/IOCs": {
"Binary ID": "ckav.ru",
"Loki-Bot Version": 1.8,
"Mutex": "706F09D9825BABF6AB8B352C",
"Potential Hidden File [Hash Database]": "%APPDATA%\\9825BA\\ABF6AB.hdb",
"Potential Hidden File [Keylogger Database]": "%APPDATA%\\9825BA\\ABF6AB.kdb",
"Potential Hidden File [Lock File]": "%APPDATA%\\9825BA\\ABF6AB.lck",
"Potential Hidden File [Malware Exe]": "%APPDATA%\\9825BA\\ABF6AB.exe",
"Unique Key": "Uzimb",
"User-Agent String": "Mozilla/4.08 (Charon; Inferno)"
},
"Network": {
"Data Transmission Time": "2017-09-19T12:32:26.429022",
"Destination Host": "obiltrate.ru",
"Destination IP": "31.31.196.236",
"Destination Port": 80,
"First Transmission": true,
"HTTP Method": "POST",
"HTTP URI": "/doit1/fre.php",
"Source IP": "192.168.1.14",
"Source Port": 49230,
"Traffic Purpose": "Exfiltrate Application/Credential Data"
}
}
{
"Compromised Host/User Data": {
"Compressed Application/Credential Data Size (Bytes)": 0,
"Compression Type": 0,
"Data Compressed": true,
"Encoded": false,
"Encoding": 0,
"Original Application/Credential Data Size (Bytes)": 0
},
"Compromised Host/User Description": {
"64bit OS": true,
"Built-In Admin": false,
"Domain Hostname": "Kelly-PC",
"Hostname": "KELLY-PC",
"Local Admin": true,
"Operating System": "Windows 7 Workstation",
"Screen Resolution": "1920x1080",
"User Name": "Grace.Kelly"
},
"Malware Artifacts/IOCs": {
"Binary ID": "ckav.ru",
"Loki-Bot Version": 1.8,
"Mutex": "706F09D9825BABF6AB8B352C",
"Potential Hidden File [Hash Database]": "%APPDATA%\\9825BA\\ABF6AB.hdb",
"Potential Hidden File [Keylogger Database]": "%APPDATA%\\9825BA\\ABF6AB.kdb",
"Potential Hidden File [Lock File]": "%APPDATA%\\9825BA\\ABF6AB.lck",
"Potential Hidden File [Malware Exe]": "%APPDATA%\\9825BA\\ABF6AB.exe",
"Unique Key": "2ztyb",
"User-Agent String": "Mozilla/4.08 (Charon; Inferno)"
},
"Network": {
"Data Transmission Time": "2017-09-19T12:32:27.079237",
"Destination Host": "obiltrate.ru",
"Destination IP": "31.31.196.236",
"Destination Port": 80,
"First Transmission": false,
"HTTP Method": "POST",
"HTTP URI": "/doit1/fre.php",
"Source IP": "192.168.1.14",
"Source Port": 49231,
"Traffic Purpose": "Exfiltrate Application/Credential Data"
}
}
{
"Compromised Host/User Data": {},
"Compromised Host/User Description": {
"64bit OS": true,
"Built-In Admin": false,
"Domain Hostname": "Kelly-PC",
"Hostname": "KELLY-PC",
"Local Admin": true,
"Operating System": "Windows 7 Workstation",
"Screen Resolution": "1920x1080",
"User Name": "Grace.Kelly"
},
"Malware Artifacts/IOCs": {
"Binary ID": "ckav.ru",
"Loki-Bot Version": 1.8,
"Mutex": "706F09D9825BABF6AB8B352C",
"User-Agent String": "Mozilla/4.08 (Charon; Inferno)"
},
"Network": {
"Data Transmission Time": "2017-09-19T12:32:27.714079",
"Destination Host": "obiltrate.ru",
"Destination IP": "31.31.196.236",
"Destination Port": 80,
"HTTP Method": "POST",
"HTTP URI": "/doit1/fre.php",
"Source IP": "192.168.1.14",
"Source Port": 49232,
"Traffic Purpose": "Get C2 Commands"
}
}
We can’t wait for the next malware analysis exercise so that we can keep learning more about looking at PCAPs for malware and honing our skills! Stay tuned to malware-traffic-analysis for the next exercise and CloudShark for our next analysis!
Want articles like this delivered right to your inbox?
No spam, just good networking