Articles
Tips for Troubleshooting Encrypted Web Applications
5 min read
As security and privacy become more important every day, the use of encrypted connections between clients, servers, and peers has been increasing at an amazing rate. With efficiency improvements to secure technologies like TLS 1.3 and easier methods to obtain certificates like LetsEncrypt, this number is only going to grow. This is a good thing for the Internet and all of its stakeholders, but presents a unique challenge for those who rely on network traces to troubleshoot and debug applications, or investigate security intrusions.
Google’s own transparency report shows that the percent of HTTPS requests made through Chrome browsers, versus HTTP requests, has doubled in the last 3 years alone.
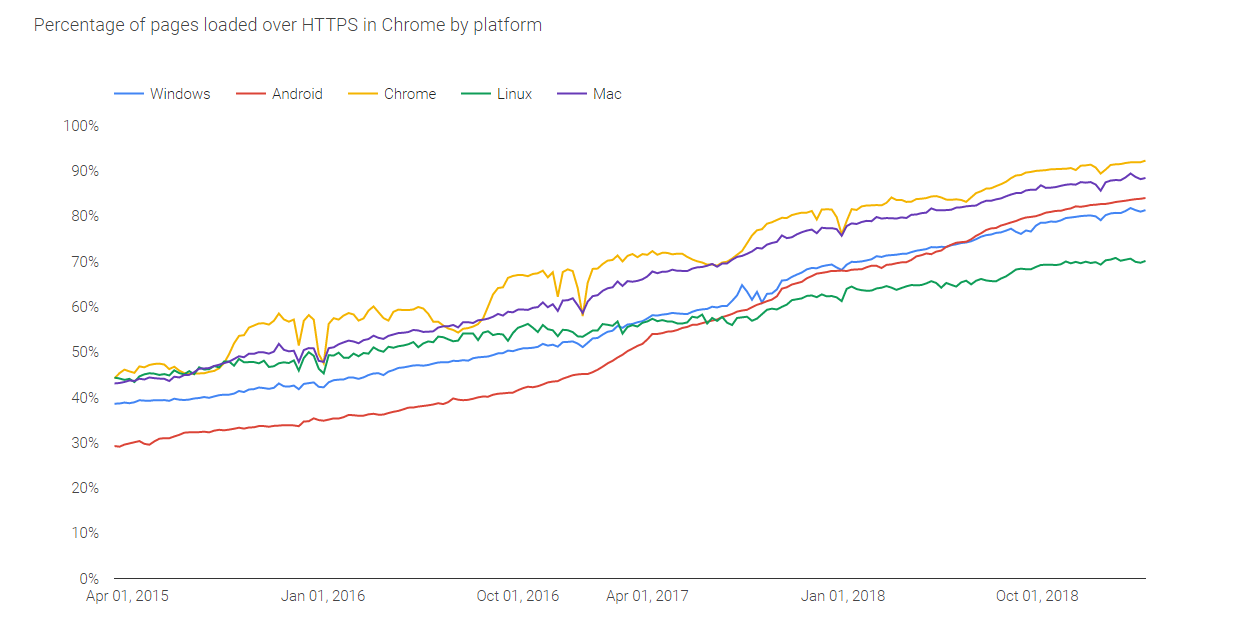
Working with captures without a system to effectively manage secure data can increase risk and threaten compliance with privacy and security standards. Without capture analysis tools that support decryption natively, it reduces the value of a type of data that should be the first go-to for any application developer, IT department, or security team.
What is TLS encryption?
Transport Layer Security (TLS) is a cryptographic protocol used to secure end-to-end communications between application layer connections. The most widely used application running over TLS is probably HTTPS (secure HTTP), used to secure web application traffic.
TLS defines a protocol for TLS Records, which handle the end-to-end transport and the encrypted payloads of a TLS connection. Before peers can send encrypted data, however, they must complete the Handshake Protocol, where the terms of the connection is negotiated.
During this negotiation the peers agree on a “cipher suite”. This is the mathematical model by which the endpoints will encrypt their data. As older cipher suites are overcome, new ones are produced that provide even greater security. These more advanced methods of encryption can make troubleshooting more difficult (and for good reason).
1. Avoid replication and sharing of decryption keys
TLS uses the Public Key Infrastructure (PKI) to encrypt data and allow endpoints to authenticate each other. These keys form the basis for encryption, and are what allow endpoints to understand the encrypted data they receive. With older cipher suites, you can use a server’s private RSA key to decrypt traffic. Newer suites that use Diffie-Hellman algorithms with perfect forward secrecy require additional keylog information from the application in order to decrypt, which means even more files to juggle just to get the job done.
This makes analyzing encrypted data risky if you or your team are relying on local applications to do so. Encryption keys are the holy grail of malicious attackers, and using a local application (like Wireshark) means each user is using and applying their own copy of a key to decrypt the data.
With an on-premises tool that can apply decryption once for all users, you’ll not only significantly reduce this risk, but make it easier for development teams to work together to resolve issues.
2. Store secure information in a single location
There’s a reason why the use of encryption is increasing - applications are passing more and more sensitive data over networks. Network packet captures, encrypted or otherwise, contain all of this sensitive data. For compliance with privacy and security regulations like PCI and HIPAA, this means they apply when considering the security of account numbers, personal information, and medical records that belong to your customers or patients.
As with encryption keys mentioned above, managing captures in a single, secure location will reduce the number of local copies of this sensitive data. On-premises tools are preferred in these cases since you can guarantee control of the system from end-to-end and make sure the data stays within your security domain.
3. Use access control to manage troubleshooting data
One of the biggest hurdles to working with encrypted data is the ability to collaborate across different teams when resolving an application or security issue. Different users from your database, development, or firewall teams all have different use cases. Not everyone needs access to this data, and often only for short periods of time. Applying access control to those captures is important if you are trying to stay compliant while still giving your teams the ability to analyze encrypted packet captures and work together while doing so.
This type of access control works even better when coordinated at both a user and group level - user-level access can prevent people from seeing data that they should not have access to, and group management helps streamline the workflow between different teams.
Using CS Enterprise for Encrypted Data Analysis
We built CS Enterprise to meet the specific challenges inherent in analyzing encrypted data for application development and incident response. This includes:
- a powerful RSA key management system that ensures that only one copy of a key exists for debug purposes, which cannot be accessed or downloaded once it’s incorporated into the system.
- the ability to apply individual SSLKEYLOG files once for all users that can access a given capture, eliminating dangerous replication of these files on local systems.
- a centralized, secure, and searchable repository for all of your capture files generated for application and security troubleshooting.
- user and group management that integrates with your existing directory systems.
As encrypted data becomes the norm, you will eventually need to handle encrypted packet captures. It’s essential to have the right tools at your disposal.
Want articles like this delivered righ to your inbox?
No spam, just good networking