Solve network problems faster with a complete collaboration solution that drastically improves results
CloudShark delivers secure storage, organization, user and group access control, and elegant, powerful analysis tools all through a web interface that enables packet analysis from any device.
A platform made for teams solving networks problemsA secure solution to organize, share and analyze packet captures
More than just a remote Wireshark, CloudShark eliminates duplicate work and streamlines investigations and reporting.
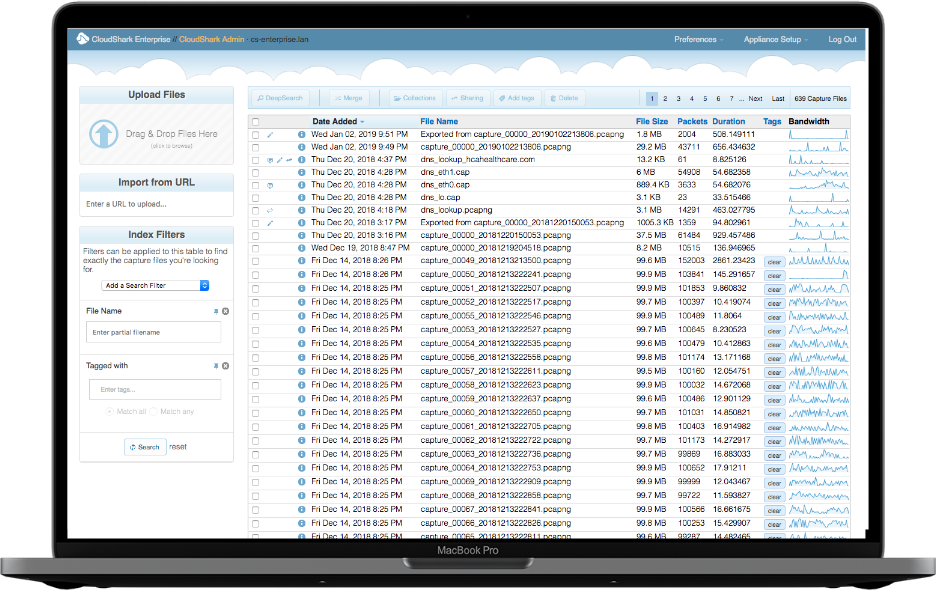
CloudShark provides a single location in your network to store and organize important trace files
UPLOAD AND IMPORT
It's easy to drag and drop capture files right into CloudShark by using your browser, but the real power comes from integrating the upload API into other tools anywhere in your network.
TAGGING
Tagging is central to organization in CloudShark. Label captures with anything that makes sense to you, whether it's location information, bug ticket numbers, or who's responsible.
SEARCH AND FILTER
Find important capture files quickly and easily by filtering on tags, size, timestamps, or by searching individual packets by display-filter.
ANALYSIS PROFILES
Build profiles to analyze specific problems and help experts and entry level technicians share knowledge and work together.
Do deep packet analysis, share your results, all without having to leave your web browser.
DISPLAY FILTERS
CloudShark supports all of the display filters that you know from Wireshark and helps you type them through autocomplete. Every analysis tool can generate a new filter with a single click.
SAVE YOUR ANALYSIS
All your analysis is saved and can be shared with a URL. Instead of reproducing analysis steps each time someone opens a file, or emailing people screenshots, link directly to it for them to see.
ANNOTATIONS ON THE PACKETS
As you do analysis, save your thoughts and notes directly on the packets as you come across them. When you or someone else comes back to the file, the annotations will be there waiting.
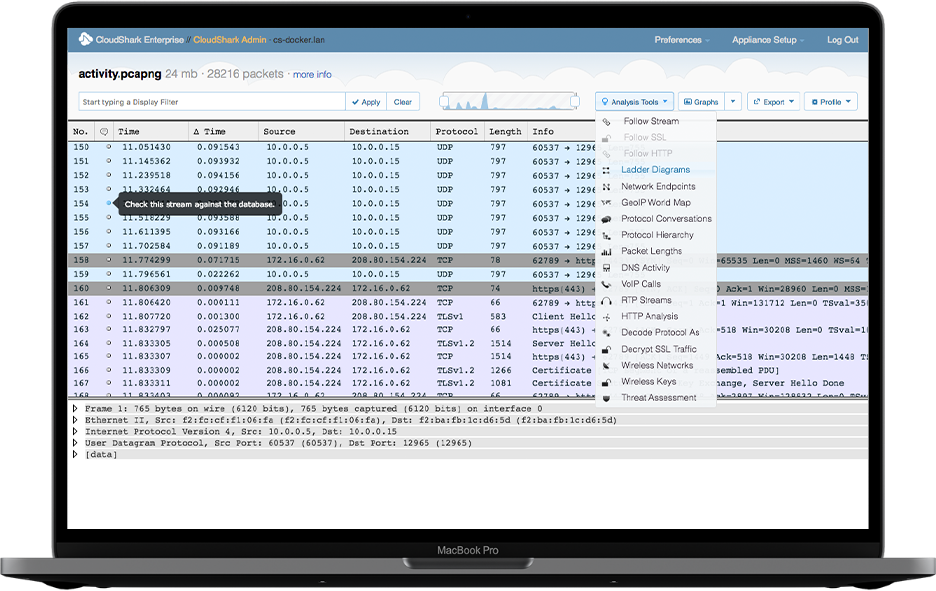
Advanced analysis tools bring you answers beyond just looking at packets.
ZEEK LOGS
See important statistics and access advanced analytics that leverage the industry standard Zeek network analysis tool. Get a high-level view of your traffic, and pivot back to the packets when you need them.
PROTOCOL LADDERS
Trace the flow of information across a single protocol or view how multiple protocols work together when troubleshooting a networking issue.
STREAM DECRYPTION
Upload session keys and certificates right to CloudShark to enable analysts to decrypt the traffic and see what's inside each packet.
SIP FLOW & RTP PLAYBACK
CloudShark has specific tools for VoIP analysis and RTP playback, including support for G.729 audio.
DNS PERFORMANCE
Look at your DNS traffic to find slow or rogue servers, unexpected queries, misconfigurations, and other issues.
MALWARE TRAFFICE ANALYSIS WITH THREAT ASSESSMENT
If you are exploring malware traffic, viruses, or other kinds of attacks, get to the bottom of an issue with the CloudShark Assessment extension.
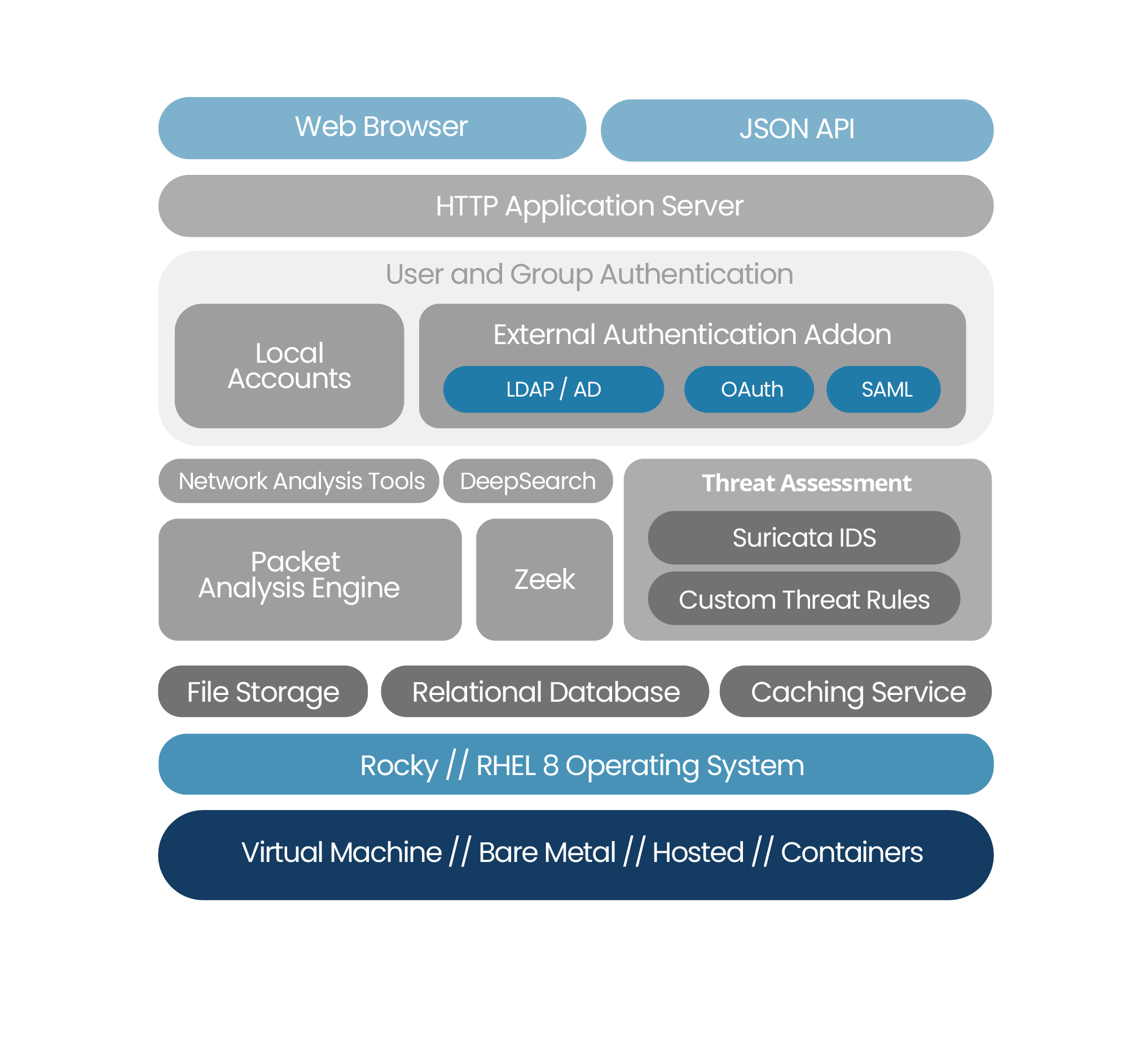
CloudShark Enterprise works in any environment.
SELF-HOSTED
CloudShark Enterprise is deployed in your own network, under your own control, in a virtual machine or on a bare metal system.
WORKS IN DOCKER WITH CONTAINERIZED COMPONENTS
CloudShark can be easily deployed in a Docker environment or as part of your network automation and orchestration.
OR, LET US HOST IT FOR YOU
Don’t want another server to administer? QA Cafe can provision, install, and manage CloudShark Enterprise in the cloud for you with no time and effort on your side.
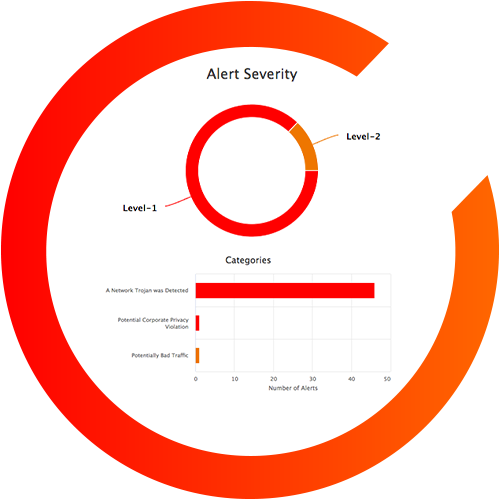
Cyber attacks today are bigger, faster, and happening more frequently than ever. Intrusion detection alerts are only the beginning of the story. You need to see the individual packet data to determine the root cause and protect your network.
CloudShark Threat Assessment is an expansion analysis tool that takes you from an IDS alert and brings you right to the packets that triggered it. Once you upload a PCAP file, you can choose Threat Assessment from the Analysis Tools menu to get a high-level summary in seconds. And, because it's built right into CloudShark, every view can be shared with your team simply by copy and pasting the URL.
External Authentication
CloudShark works with your existing network directory services such as LDAP or Active Directory, making it easy to manage users and groups.
Expanded User Pack
Have a sizable team or customer base? CloudShark licenses are priced in units of 25, 50, 100 users or something custom for your team.
Looking for integration opportunities?Add secure integrated packet analysis with Packet Viewer!
Packet Viewer is built from the power behind CloudShark and easily integrates directly into your existing solution and brand, enhancing your product with a familiar and comprehensive packet analysis experience.

MINIMAL DEVELOPMENT
Quickly enhance your solution’s capabilities with Packet Viewer’s easy-to-integrate components.
Learn more
SIMPLE LICENSING
Packet Viewer’s OEM licensing is simple. No nickel and diming your team after you've committed.
Learn moreConnecting the dotsDiscover how CloudShark is helping our customers improve network troubleshooting & investigation
Articles
How do packet captures affect cybersecurity framework compliance?
February 03, 2021 · 6 min readNetwork packet captures present a unique challenge to CIOs and CISOs when considering cybersecurity framework compliance like those outlined by NIST or the DHS Cybersecurity and Infrastructure Security Agency (CISA) Trusted Internet Connections program.
Case Studies
Beeks Financial Cloud incorporates CloudShark into their solution to revolutionize financial network analysis
February 08, 2021 · 3 min readOur case studies usually focus on end-users of CloudShark, but our recent integration with Beeks Financial Cloud was a great opportunity to show just how easy it is to work with us here and incorporate CloudShark into your products to get the most out of working with captures.
Webinars
Cutting Through Network Forensic Data With Zeek
February 08, 2021 · 1 min readZeek (formerly Bro) is a powerful tool trusted by networking and cybersecurity experts for analyzing network traffic. By creating collated, organized records of network activity (called “logs”), Zeek gives the network analyst a new approach when dissecting and investigating traffic.

Talk to an expert
Our team is happy to answer your questions or give you a demo. Click below to tell us a bit about yourself and we will get in touch!
Let's chat